Security researchers have revealed the Zombieload Attack to the public. In brief, the Zombieload Attack allows the stealing of sensitive data and keys while your computer accesses them. Reminiscent of Meltdown and Spectre, Zombieload exploits a weakness in speculative execution. However, this is a brand-new side-channel attack which relies upon four Intel CPU design flaws that weren't patched up in the wake of previous scares.

Let us start by looking at what particular hardware is vulnerable. The majority of Intel processors dating back to 2011 are said to be affected by the constituent bugs that allow the Zombieload Attack to operate with success. Some relief for Intel is that many of its latest processors in the 8th and 9th gen processors families are safe from the exploits which allow the Zombieload Attack.
Patch = performance hit
Intel has provided a lookup table in a PDF, listing a huge number of its processors. I found my Haswell i7 desktop CPU in the processor tables and it seems that it is vulnerable to what Intel calls 'Microarchitectural Data Sampling' bugs, and that Intel is working on an update which can be delivered via microcode updates. Intel admitted in a call to TechCrunch that "the microcode updates, like previous patches, would have an impact on processor performance". In a worst case scenario consumers are said to be looking at a 3 per cent performance hit. It could be worse in the enterprise market, up to a 9 per cent performance hit.

If you are interested in how attacks like Zombieload work with the newly revealed hardware vulnerabilities, it sounds similar to the way that Spectre and Meltdown attacks work. In Intel's own words, four processor architecture features (Store buffers, Load ports, Fill buffers, and Uncacheable memory) on processors which utilise speculative execution "may allow an authenticated user to potentially enable information disclosure via a side channel with local access".
To exploit the vulnerabilities hackers would have to get some malware onto the user system or enterprise server. In this case "user-level secrets, such as browser history, website content, user keys, and passwords, or system-level secrets, such as disk encryption keys," will be possible to purloin.
The video above shows "how an attacker can monitor the websites the victim is visiting despite using the privacy-protecting Tor browser in a virtual machine."
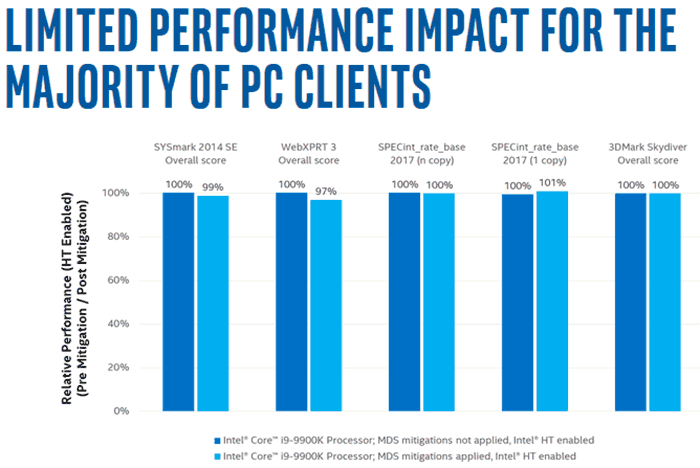
UPDATE:
Intel has shared a blog post which contains performance graphs seeking to illustrate the "limited performance impact for the majority of PC clients" in applying security patches against the Microarchitectural Data Sampling (MDS) bugs. An example chart is reproduced below. This is just one of four charts shared by Intel and note that it is based on tests on 9th gen Core processors.