It has emerged that US travel giant CWT has paid a $4.5 million ransom to hackers who leveraged a strain of 'Ragnar Locker' to make terabytes of files inaccessible and knock thousands of corporate computers offline.
In case you haven't heard of CWT, it is a sizable US business which manages travel for more than a third of companies on the S&P 500 U.S. stock index and posted $1.5bn in revenue last year.
Reuters reports that the hacker cybercriminals got in touch with a representative of CWT, after their dastardly deed had been done, to negotiate a ransom. Initially a sum of US$10 million was demanded for the safe return of "reams of sensitive corporate files," and the deletion of copies of the data. It isn't clear if the data was mainly CWT's its customers' or both - reporting organisation Thomson Reuters is a customer of CWT. The hackers suggested paying them off would be much cheaper than the law suits that would result if they leaked all this data publically.
After some negotiation the CWT rep, said to be acting on behalf of the CFO of the company, OKed a sum of $4.5 million to be paid to the hackers via Bitcoin. This sum, 414 Bitcoins, was sent to the hacker digital wallet on 28th July.
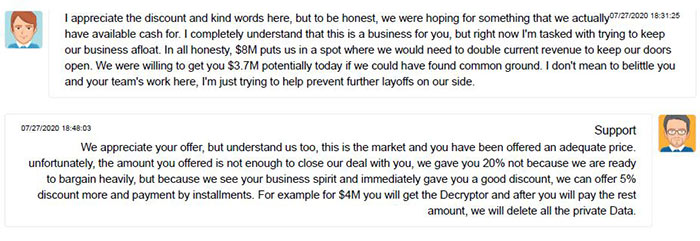
Reuters European Cybersecurity Correspondent, Jack Stubbs, shared some more fascinating background information about this cyber heist via his Twitter account. Unusually, the ransom negotiations took place in a chat room which was open to the public, and it provides some insight into the proceedings. One example is given above.
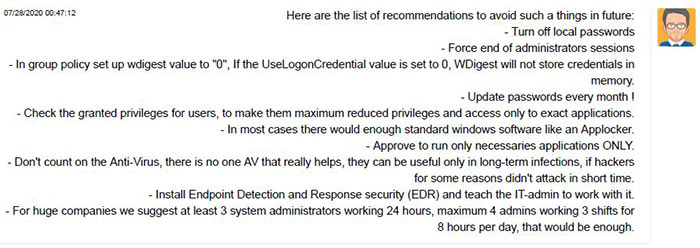
After the ransom was paid up, the hackers kindly provided some recommended security advice, including appropriate staffing practice.
Cybersecurity experts recommend thorough protected backups to avoid being prey to such crypto-locker ransom demands. Furthermore, payment of ransoms is discouraged as it will help perpetuate this underhand business.













