Asus computers which use or ship with Asus Live Update software installed are at the centre of a new computer hacking story. A recent report by Motherboard reveals that hackers managed to sign some malware with a legitimate Asus digital certificate and then uploaded it to Asus' download servers, where it was hosted for several months last year. This software was installed by default on numerous Asus computer models.

Kaspersky says that it discovered this "sophisticated supply chain attack involving the ASUS Live Update Utility" in January. A large number of users have been affected, says the security firm's blog, which is understandable given that Asus is the world's 5th-largest PC vendor. It estimates that over a million users worldwide possibly ran a computer with this backdoored software update utility. The dodgy software was undetected for so long as it was legitimately signed and hosted on the official liveupdate01s.asus.com and liveupdate01.asus.com Asus update servers. It was hosted there between June and November 2018.
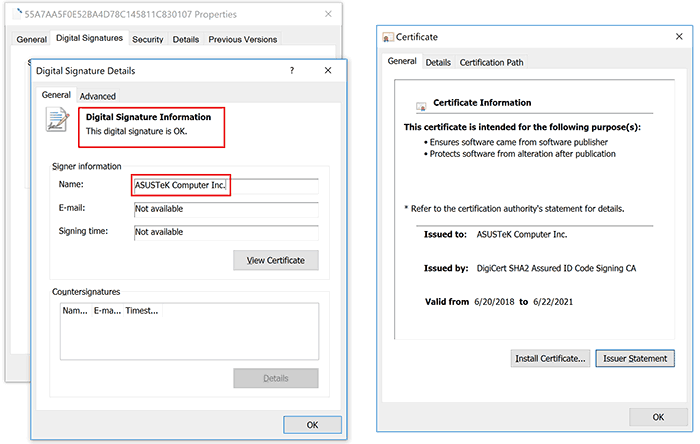
Digital signature on a trojanized ASUS Live Update setup installer
Certificate serial number: 05e6a0be5ac359c7ff11f4b467ab20fc
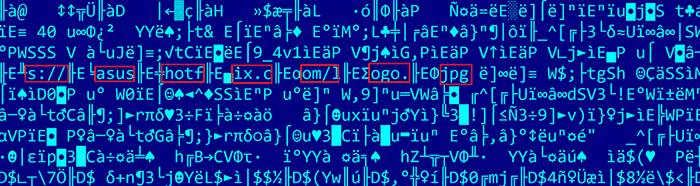
Interestingly the Asus Live Update malware attack was targeted at a pool of users identified by a limited range of network adapter MAC addresses. Kaspersky found more than 600 unique MAC addresses from over 200 trojanised samples used in this attack. If a match was found to one of the 600 MAC addresses the computer would download some software from asushotfix.com, "a site masquerading as a legitimate ASUS site, to fetch a second-stage backdoor that it downloaded to that system," explains Motherboard. The asushotfix.com site was closed in November last year, before discovery of this hack, thus researchers are unable to obtain a copy of the second-stage backdoor file pushed out to victims, or identify victim machines that had contacted that server.
Asus was informed of the issue on 31st January 2019. If you are interested to see if your Asus computer is one of the "surgically selected targets of this attack," you can check whether your MAC address has been targeted by the 'ShadowHammer' attack here.
It is believed that the ShadowHammer attackers were behind the ShadowPad and CCleaner attacks and that they gained access to Asus servers via the latter, as Asus was a primary target of the CCleaner attack.
Kaspersky's investigations are still in progress but it says it will present full results and a technical paper during the SAS 2019 conference in Singapore (8th-11th April).
UPDATE
Asus has responded to the above.
It has created a diagnostic tool (zip download).
There is a fix in the latest version of Live Update (ver. 3.6.8).













